[Update: Singapore Airlines has responded to Ms Low informing her that they will be reinstating the lost miles, and that they are working to implement an OTP feature, but do not have a fixed date for implementation. That’s certainly a relief, and can’t happen soon enough]
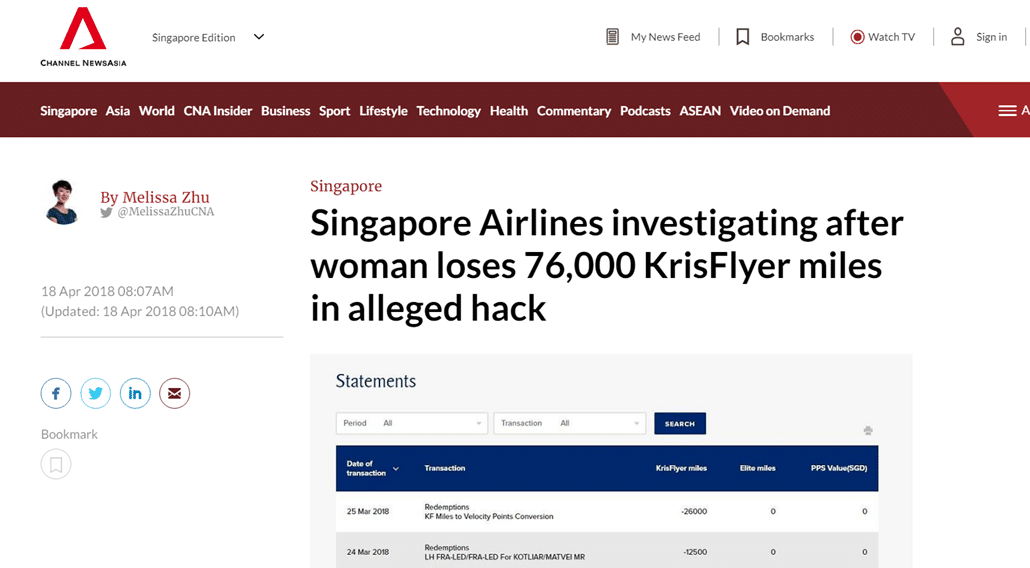
Today’s CNA reports the case of a KrisFlyer member who lost 76,000 KrisFlyer miles in an alleged account hack. Ms Low, a 34 year old general manager, discovered on 15 April that the majority of her account balance had been cleared out by five fraudulent transactions that took place on 24 and 25 March.
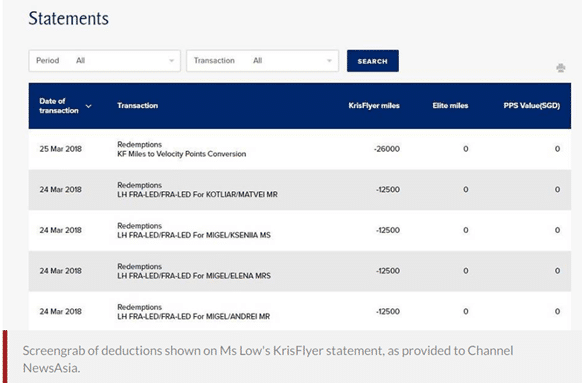
The perpetrator redeemed four one-way economy class tickets on Lufthansa from Frankfurt (FRA) to Saint Petersburg (LED) at 12,500 miles each, before transferring a further 26,000 miles to Velocity. In total, 76,000 miles were emptied out in two days.
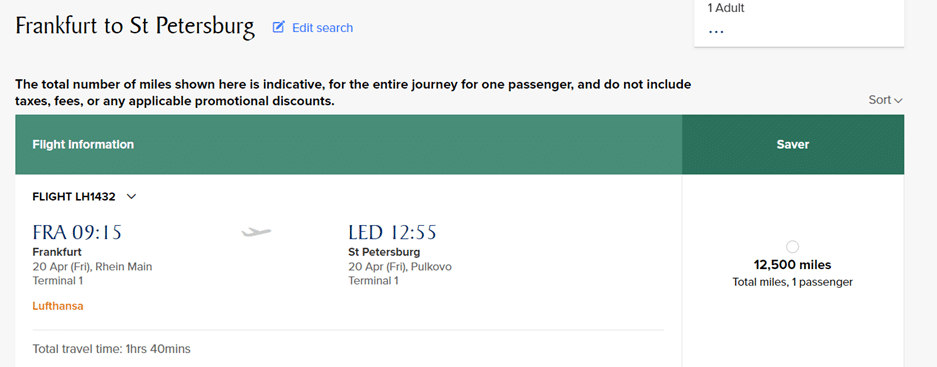
This has all the hallmarks of a classic account breach. Points are transferred out quickly to other partner accounts (eg Velocity) where they are redeemed quickly, or used to redeem one-way flights on partner airlines. The presence of partner airlines and accounts complicates any recovery attempt, which is deliberate on the part of the hackers.
Now, we don’t know what date those partner award tickets were set to fly, but given the redemptions happened on 24 March and the hack was only discovered on 15 April, I’m almost 100% certain the flights have already been flown, and I’m pretty sure the reason that KrisFlyer membership services is telling Ms Low that they don’t want to give her “false hope” that she would get her miles back is because once those flights are flown, any recovery is very messy. Lufthansa has already incurred the costs of flying those passengers, their systems will request a certain amount of reimbursement from KrisFlyer to cover the cost, and unless SQ is willing to eat that cost, no miles can be refunded to Ms Low.
What this incident points to more broadly, however, is an alarming lack of account security at KrisFlyer.
Who is at fault?
I reached out to Ms Low, who says she has no idea how her account was compromised. She says she is very certain she was not the victim of phishing, has never revealed her password to anyone and has only ever logged into her KrisFlyer account through the official website. She also concedes that there were indeed alerts about the redemptions sent to the email address linked to her KrisFlyer account, but the email account was inactive and she did not check it.
There are some who will point to this and say Ms Low has to shoulder some of the blame for the incident, insofar as she did not exercise vigilance. I don’t disagree; I think that’s a major oversight on her part. However, what is more concerning to me is that a properly designed system should not have allowed what happened to Ms Low to happen in the first place.
Strong security systems are based on “something you know” (a password), “something you have” (an OTP token) and “something you are” (biometrics). We’re not yet at the stage where biometrics can be easily integrated into the security process of frequent flyer accounts, which means we all the more need to double down on ensuring that the “something you know” and the “something you have” are as strong as possible. In the case of Singapore Airlines, the “something you know” aspect is extremely weak, and the “something you have” aspect does not exist.
Six digit numeric passwords are woefully inadequate
Singapore Airlines’ response to CNA’s enquiries was almost laughable:
“We have also reached out to the affected members and advised them to take various measures to prevent further phishing. These include using stronger passwords, changing their passwords regularly, using a reliable anti-virus programme and logging in to their KrisFlyer accounts only via the official SIA website at www.singaporeair.com.
“Using stronger passwords”. Guys, your system asks for a six digit PIN. A six digit PIN is woefully inadequate to protect an account, and there is no such thing as a “stronger six digit PIN”.
There are numerous sites that let you test how strong your password is. Here’s how long it would take a computer to brute force the password I use for my Asiamiles account: (minimum 8 characters, minimum 1 upper-case letter, minimum 1 number, minimum 1 of the following special characters: !, #, $, ^ or *)
And my corporate email (minimum 8 characters, minimum 1 upper-case letter, minimum 1 number):
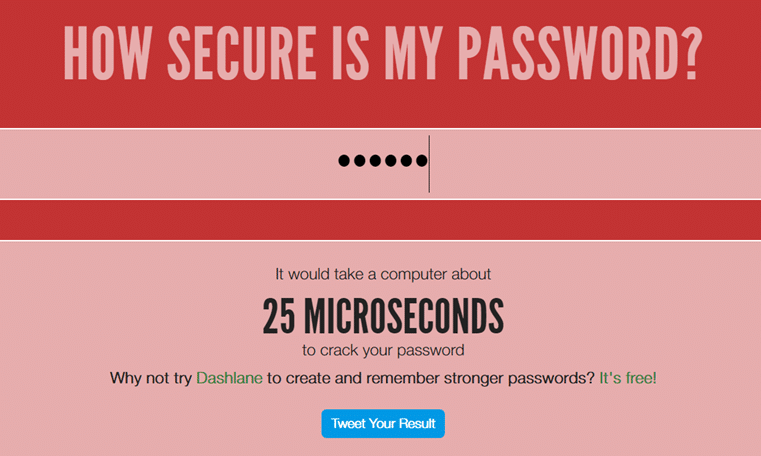
And my KrisFlyer account (minimum/maximum 6 numeric digits):
And no, my KrisFlyer PIN is not 123456 or any string of the same six digits. Try entering that and you’ll see it would be cracked instantly. My completely random six digit KrisFlyer PIN can be cracked in 25 microseconds. Clearly, something is wrong here.
Remember Hilton? Back in October 2014, Hilton suffered a major account breach in which many Hilton Honors accounts were emptied out of millions of points. The cause? Hilton had a 4 digit PIN password policy.
You’d think other companies would have learned from that incident (Hilton later updated its policy to require stronger passwords, rewarding members who set them proactively), but no. IHG, frustratingly, still uses a 4 digit PIN policy (Mark from The Shutterwhale got hacked recently), and KrisFlyer’s 6-digit PIN policy is a breach just waiting to happen.
No One Time Passwords (OTPs) for high risk transactions
Weak password policies are one thing. But the lack of an OTP for high risk transactions only compounds the problem.
I’m no security expert, but I’m quite certain the gold standard for security is to require an OTP before any high risk transactions are done. Banks do that, which is why when you want to add a new transfer recipient on your iBanking you’re prompted to enter an OTP. We even see this on other “less sensitive” apps like Chope. When I want to redeem my Chope Dollars for an award, I need to enter an OTP that is sent to my verified mobile phone number.
To be fair, OTPs for high risk frequent flyer account transactions (such as redemptions or adding of nominees) are not standard practice among airlines yet (Qatar Airways being a notable exception), but other airlines mitigate these risks somewhat by having strong password requirements.
When you take a program like KrisFlyer with a 6 digit numeric password and combine it with the lack of an OTP, your problems just get multiplied. There is understandably some cost involved in setting up an OTP system, but given the sheer volume of members and transactions that KrisFlyer has, surely it makes sense to have these safeguards in place?
As it is, the current Krisflyer security process is set up for failure, and that’s on Singapore Airlines. Yes, individual members need to take responsibility to protect their passwords and accounts. But the hallmark of a good system is it protects users from themselves. A hacker who obtains the password of a user should still be met with further challenges from the system when he/she tries to carry out high risk transactions, and that’s not what happened here.
Mileage brokers, again
Let’s come back to what happened to Ms Low. Before anyone tries to dox the four redemption nominees (whose names are clearly seen in the screenshot provided to CNA), I’d like to point out that I am very certain they’re not the ones who compromised her account. In all likelihood, her account was hacked by a mileage broker.
Back in August 2016 I wrote an article about so-called mileage brokers (a long article, but I’d strongly encourage you to have a read) . Mileage broker ads often appear on Google and other advertising networks- they’re the ones shouting CHEAP FIRST AND BUSINESS CLASS TICKETS!!!
Mileage brokers entice customers with the promise of deeply-discounted air tickets. When a customer agrees to buy from them, the brokers redeem miles for the ticket in the customer’s name and send the ticket to him/her, or transfer miles to the customer so he/she can do it him/herself.
Where do those miles come from? There are two M.O’s of mileage brokers:
- Buy miles/credit card points from those who have no use for them. This is a willing buyer, willing seller arrangement
- Use compromised frequent flyer accounts to redeem award tickets on behalf of the customer, without the knowledge of the account holder. In these situations, the travel date will presumably be very close to the redemption date (sometimes on the same day) to minimize the likelihood of the account holder finding out and flagging it
(1) is against the T&Cs of airline frequent flyer programs, and your account can be shut down with all miles confiscated if it’s found out that you bought/sold miles, or that you redeemed tickets with miles transferred in from a third party. It’s not illegal per se (doing this does not break the law, just the T&Cs of the airline FFP) but I still believe it’s wrong because it penalizes rule-abiding FFP members who need to compete with these brokers for awards
(2) is obviously a felony, and you’re liable for criminal prosecution if it can be shown you hacked someone else’s account or were knowingly involved with a hack. On the dark web, you’ll find brokers offering to sell entire airline or hotel frequent flyer accounts with lots of miles and points in them.
In any case, Ms Low’s redemption nominees probably have no idea what happened. All they know is- they bought a deep discount economy flight, the tickets came through, they flew successfully (presumably) and that’s the end of the story.
I investigated the mileage broker story for about a month, setting up a dummy KrisFlyer account (hello, Niole Lim!) and successfully purchasing miles from several brokers.
Normally, this should not even be possible, because the back end should be checking if there is a conflict between the name of the person transferring and person receiving (this is to prevent a secondary market for miles from springing up). However, my transfers went through flawlessly. One broker even told me he had access to “hundreds” of KrisFlyer accounts.

Long story short, I wrote to KrisFlyer on 11 August 2016 with the results of my investigation, highlighting the shortcomings they had in their verification and security processes. On 12 August I received a note from them requesting more information, which I provided on the same day. Then I waited for them to confiscate the miles and shut down my dummy account.
13 days passed after I told them outright what I had done, and my dummy account was still fully active and able to transact. On 24 August I wrote to them again to ask what was happening. I waited some more. 10 days later, I got a reply from KrisFlyer that didn’t really explain anything:
You have confirmed that all KrisFlyer miles in your account 8XXXXXXXXX (2,000 KrisFlyer miles) were purchased from online mileage brokers. In view that this contravenes the KrisFlyer programme rules, we regret to inform you that your KrisFlyer account has been suspended pending audit checks and the miles will be forfeited.
I mean, sure, take the miles, I knew from the start that the money I paid to research the article was going to be a write-off. But they didn’t actually explain what they were going to do to secure their systems. They were telling me what I already knew- that I had been a very bad KrisFlyer member and my miles were now going bye-bye.
It gets better. Even after that email, my dummy account was still not shut down! As of 7 September, a full 27 days after I first contacted KrisFlyer, Niole Lim’s KrisFlyer account was alive and well and able to transact as per normal.
The account was eventually shut down a few days after 7 September. But if this is the laissez faire attitude that Singapore Airlines has towards fraud and account security, it’s no wonder that something like this happened.
For the record, I sent SQ one more email asking what they had done to improve their anti-fraud policies, but received no response or further communication on the matter.
Conclusion
Krisflyer has big technology plans for the future. For example, they want to digitise miles and deploy a blockchain-based digital wallet app. One hopes they would have somewhat more robust security protocols when this comes to market, because based on current evidence there’s very little reason to have confidence.
Should Ms Low be reimbursed for this fraud? That’s a tricky question. Some will point to credit cards where cardholders are generally not liable for more than $100 of fraud provided it can be shown they exercised due care in protecting their personal information. This situation is a bit different, though, given that there is no framework that governs frequent flyer programs and it’s entirely at the discretion of individual airlines to develop and enforce policies regarding fraud protection (versus the banks where the ABS stepped in to require all to have the $100 cap).
Without knowing the full facts of the case I won’t venture a definitive answer here except to say that if SQ’s investigation shows that the account holder acted with all due care, then it’s my belief that the miles should be reinstated, even if that ends up costing the airline out of pocket. Fraud is an unfortunate cost of doing business for any company, and it’s their duty to harden their systems to make it more difficult. This is all the more the case if it’s shown that her account was breached through a brute force hack, because that is entirely the fault of SQ for not allowing stronger passwords. If nothing else, SQ will come out looking slightly better for standing up for one of their customers.
Again, let me emphasize that this does not absolve the individual of personal responsibility. My response would be quite different if the investigation shows otherwise. Regardless of whether Ms Low is reimbursed, however, SQ urgently needs to upgrade its password protocols for KrisFlyer.
As it is, there are a lot of unanswered questions now. Have more KrisFlyer accounts been compromised? Have there been other cases that have not yet come to light? I don’t know, but I’d encourage you to change your PIN if you haven’t done so in a while, and hope that KrisFlyer takes the necessary steps to beef up account security.












I agree with you 100% and good on you that you attempted to get them to do something about it back then, although really sad (and sickening) that they didn’t think it serious enough to actually do something about it. Let’s see if someone finally picks up the ball or not!
I happen to chance upon this article and I went through the same thing of being hacked (even though in my case, there is no transaction because I just made a big redemption) My account was first hacked into, and the hacker changed my email, phone number and password which effectively locks me out. Upon that, it took SQ 2 days to give me a new account. I asked for my existing flight to be transferred but it was not (more later) With my new account, it was hacked again. This time round, the hacker failed. Upon resetting my pin… Read more »
sorry to hear about your experience. the existing a380 business class seats are indeed well worn, but the new a380 business class is pretty incredible.
my wife & my account were “under review” until this morning too.
sq new a380 business class is over rated. sleep diagonally and expensive price tag to match does not compete well with QR/AF.
if is at own expenses i would have spend it elsewhere.
When they meant suspended, I think they meant that you will not be able to redeem your miles rather than the whole account being shut down. I had miles transferred from my dad’s UOB account to mine and I could still use the account. I was not able to redeem for any flights however until investigation was completed.
Hi Aaron,
I love the investigative journalism work that you have done here. Kudos to your perseverance in wanting to establish a more secure system for mile lovers.
thanks alison! let’s hope they pay attention this time
She loses 76,000 miles. I work on the theory that banks buy miles for about 1c to 1.5c, based on 2 things: – SQ’s points plus cash redemption rate is about 1 mile = 1c – UOB, DBS, Citi all offering cards with 1.2-1.4mpd, compared to StanChart and Maybank with 1.5-1.6% uncapped no minimums cashback So to reinstate these miles, it would cost SQ around $760 to $1140 using my theory. Not a lot of money to avoid this sort of PR. Instead we get to see them try to weasle their way out of committing to restore the miles… Read more »
i actually think this is more about precedent. SQ is worried that if they reimburse her, they’ll have to do the same for every case in the future. my point is: had they beefed up their systems and made this sort of thing difficult to happen, they could mitigate the issue.
Then they seem to have had some practice in dealing with this. One thing about passwords, I hate the overly restrictive password requirements, like Asiamiles where you need at least 8 characters, capital, lower case, numbers, special characters all whilst doing a handstand on the branch of a bonsai tree. On top of that, if you forgot your password, you can’t reset to an old one. Pain in the bum, I will forget my password again with them and just set even more obscure and random passwords that I will forget even quicker to the point where the whole authentication… Read more »
Yes. Try entering wrong password in your KF account now and see what it says.
I didnt want to test locking out my account, I got some redemptions coming up shortly!
Bad publicity still free publicity I suppose.
Well weird to see SIA still cheapo to it’s Singapore roots.
Yep, much of SQ’s woes come from being cheapskates; yet like much of corporate Singapore they spend big on ‘outside’ consultancies and image items. Analogy: they count the used pencil stubs and loo paper when it comes to pax and staff down the totem pole, but drink Petrus themselves!
Just tried changing the password and a few things hit me. 1. Thanks to SQ’s 6 digit pin policy, many of the people I spoke to today used their date of birth DDMMYY as their pin. While it’s not a “scientific survey” with numerous data points, it does point to how people generally take the easy way out when it comes to choosing passwords. 2. We quote our Krisflyer number at many places (ex: Hertz, partner airline, hotel check-ins, etc). And we also provide a copy of our passport at many of these places. Getting hold of DoB is extremely… Read more »
It’s not just the miles. A lot of customer info stored on KF. Ripe for the taking.
To me SIA is run by a bunch old minded folks who have yet evolved and still think they can thrive using Jurassic practices in the new millennium age. This is a classic example like what happened in the US when the senate quiz Zuckerberg, they were totally lost and clueless and Zuckerbergpretty much ran their coat tails.
Most classic MNCs are just doing the basics and fighting fire with a water pistol and have no idea how the new world works
Let’s also not forget that (until recently*) every email advertisement flyer that Krisflyer sends you, your krisflyer account number is displayed on the top right hand corner. Now this might be one of those ‘reference’ number fields automatically inserted into emails, but it shows how accessible your KF number is – who knows? Promotion email flyers could be forwarded to some one willy-nilly.
Surely banks don’t print your account number on any CC promotional materials they send you, no?
*KF membership number was still appearing on the ad email announcing the new 787-10 – go look.